
Make it easy for your customers & set your teams up for success


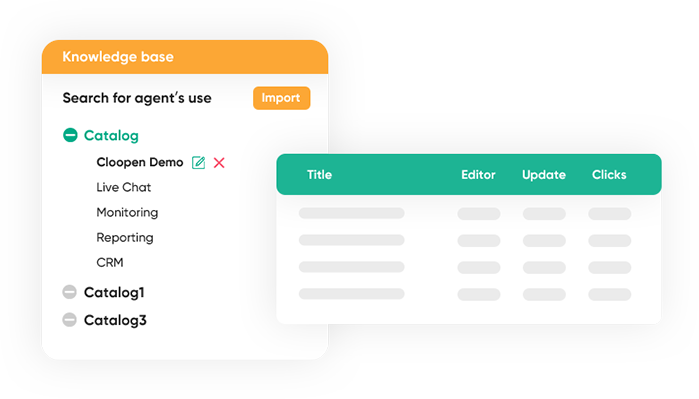


1Demand combing
2Solution design
3Online deployment
4Test & Acceptance check
5Use training
6Follow up/ Revisit/ After service
IP whitelist management to avoid brute force cracking of login
TIS transport layer protocol to avoid snooping.
Interface vulnerability scanning to avoid illegal request attacks.
DB data files are stored encrypted to avoid clear text leakage of DB data.
Develop code review and release process system to avoid human non-security bugs.
7*24 monitoring + O&M security management system to reduce the impact of accidents for the first time.







Be a leader of communication serviceprovider who aims to revolutionize the communication industry.


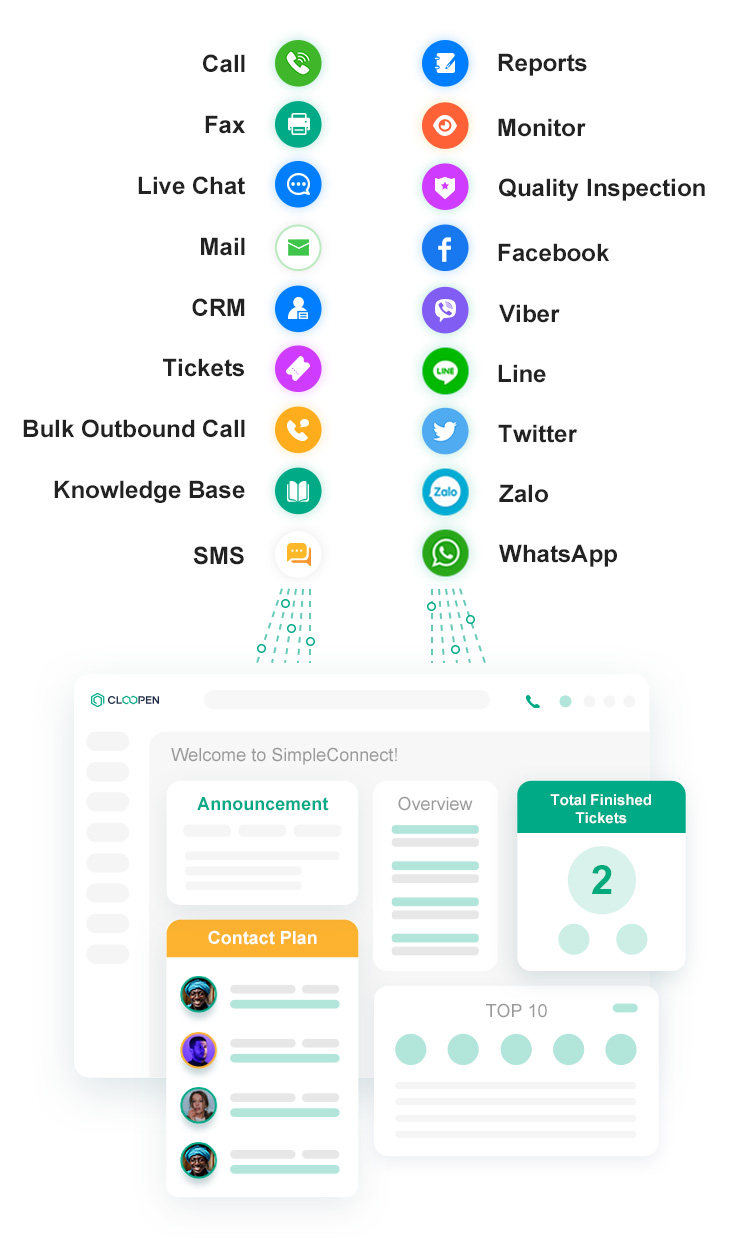
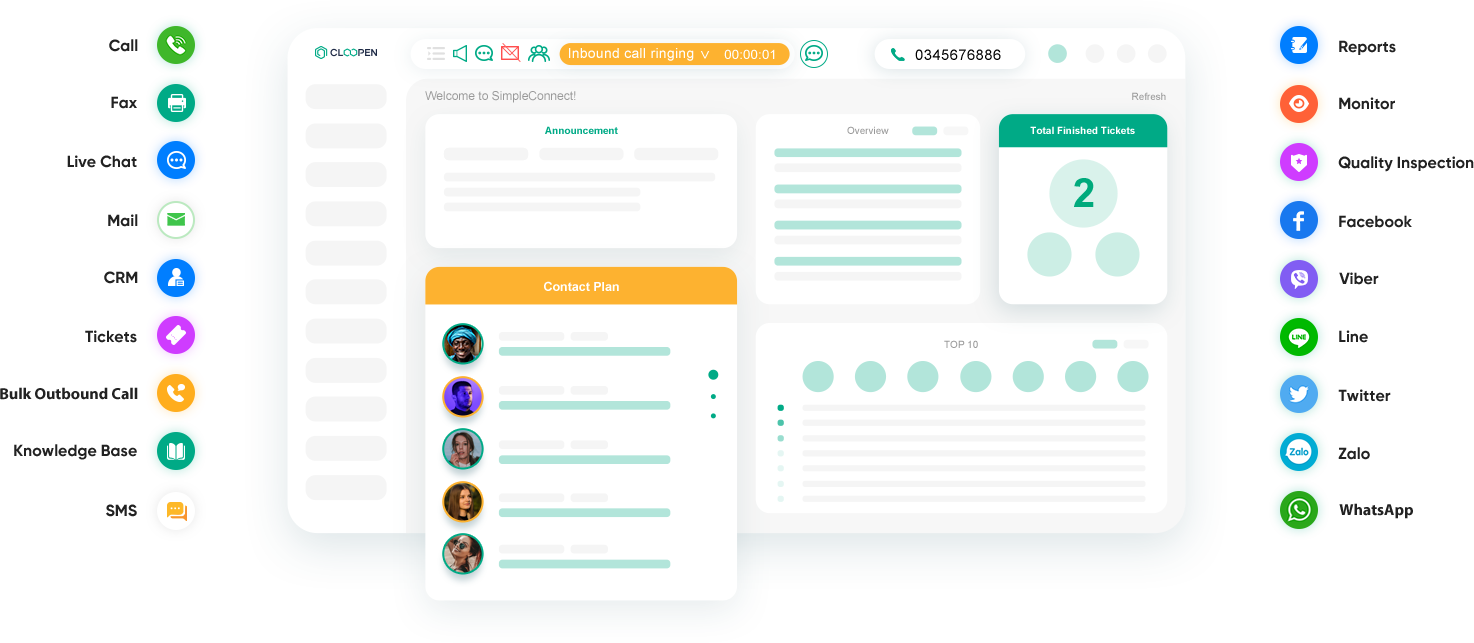
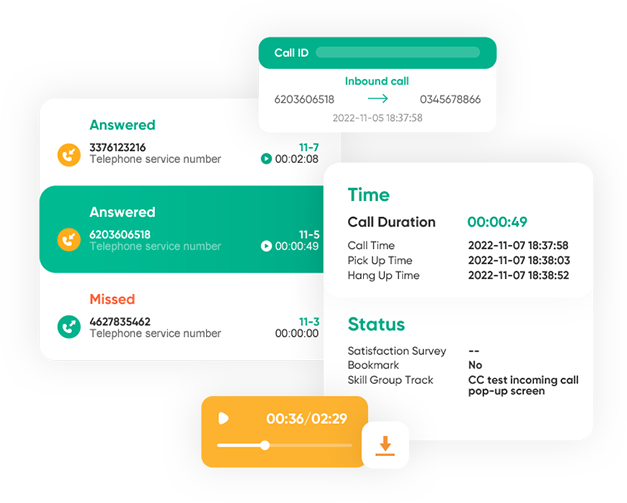
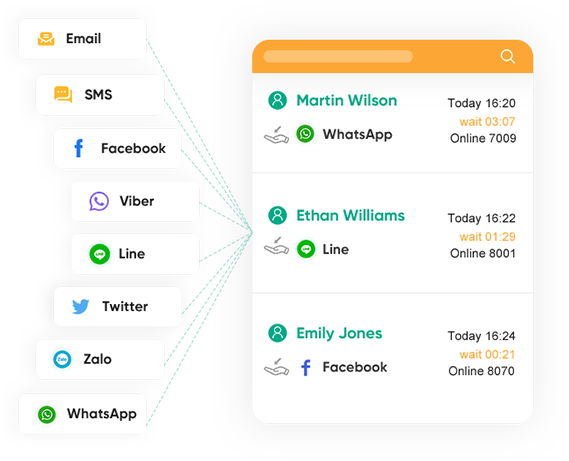
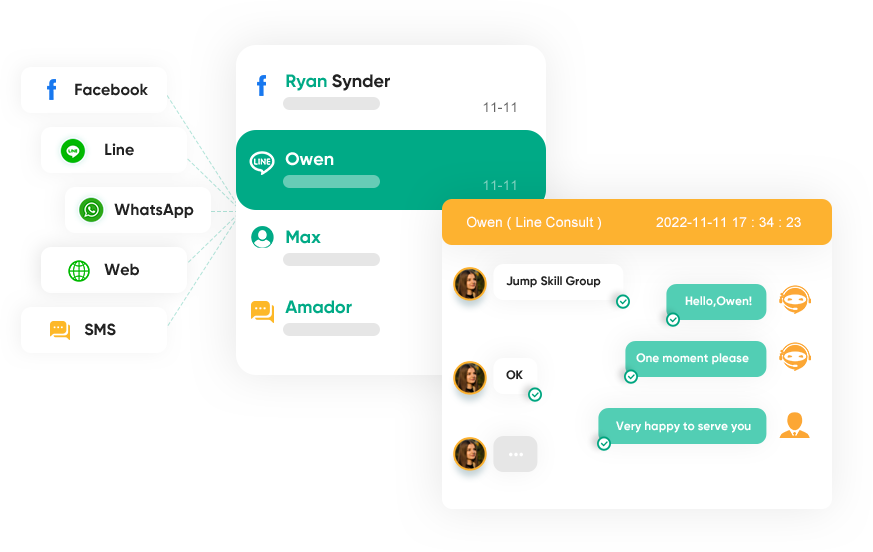
Get one-stop service, interact with your customers whenever and wherever they prefer